If you rely on encryption to protect your business, you should be asking a simple question: what is quantum computing and why are security experts treating it as a game‑changing risk? Quantum machines are not yet common, but the race to build powerful systems is moving fast, and decisions you make today may decide whether your data stays safe tomorrow.
What Is Quantum Computing? Simple Explanation for Security Teams
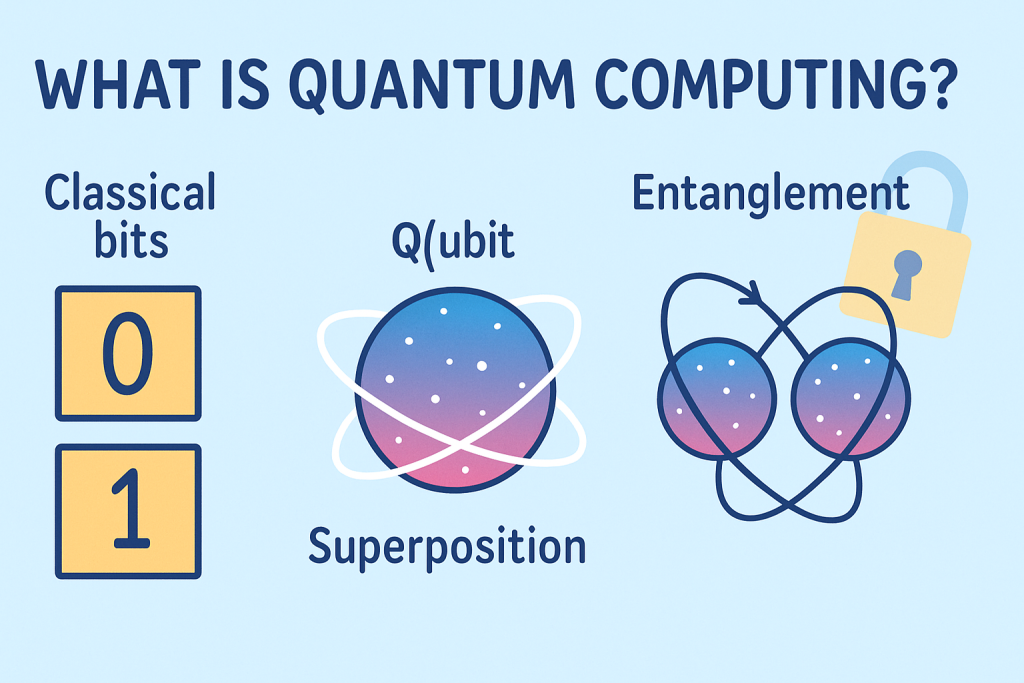
To understand what is quantum computing, think about how today’s computers work. Traditional systems process information in bits that are either 0 or 1. Quantum computers use quantum bits, or qubits, which can be 0, 1, or a combination of both at the same time. This property, called superposition, lets quantum machines explore many possible answers in parallel.
Qubits can also be linked together in a special way, known as entanglement. When qubits are entangled, a change to one can instantly affect the other, even if they are far apart. This gives quantum computers a powerful way to coordinate calculations that would take classical machines an extremely long time.
In simple terms, when we ask what is quantum computing, the answer is that it is a new way of processing information based on the rules of quantum physics. This new model allows certain problems to be solved far faster than with traditional computers, especially problems that involve searching through huge numbers or complex patterns.
How Quantum Computing Works (Without the Math)
Quantum computers are built from qubits that must be carefully controlled. They are very sensitive to heat, noise, and interference, so most quantum systems operate in highly protected environments. Specialized hardware and error‑correction techniques are needed to keep qubits stable long enough to run useful programs.
Quantum algorithms tell the machine how to use superposition and entanglement to solve specific tasks. Some algorithms are designed to search large databases more efficiently, while others can factor large numbers or simulate molecules. When we explore what is quantum computing from a practical viewpoint, the key idea is that quantum algorithms can shrink tasks that would take classical computers an unrealistic amount of time.
For online security and cybersecurity teams, the most important category of quantum algorithms are those that weaken or break today’s encryption standards. This is where quantum computing in cybersecurity shifts from a research topic to a direct business risk.
Why Quantum Computing Matters for Cybersecurity
So far, we have focused on what is quantum computing and how it works at a high level. Now we need to look at why it matters so much for encryption and data protection.
Most secure communication on the internet relies on public‑key cryptography. Popular methods, such as RSA and elliptic curve cryptography, depend on the fact that certain math problems are hard for classical computers to solve. A well‑designed key is meant to be out of reach for any realistic attacker.
A powerful quantum computer can change that assumption. Quantum algorithms exist that could, in theory, break many of the public‑key schemes that protect web traffic, VPNs, secure email, code signing, and more. Once an attacker can use a quantum machine to solve these hard problems, they can:
Recover private keys from public information
Impersonate websites, users, or services
Decrypt captured traffic that was recorded in the past
Break digital signatures on software, documents, or updates
This is why you will hear experts talk about the “harvest now, decrypt later” threat. Attackers can store encrypted data today, then wait until quantum computers are strong enough to break the keys. When leaders ask what is quantum computing doing to my risk profile, this delayed danger is one of the most important points to understand.
Data at Risk Across Industries
For many organizations, the most exposed data includes:
Long‑lived secrets such as root certificates and certificate authority keys
Sensitive personal data that must remain private for decades
Intellectual property such as designs, formulas, and source code
Government, defense, and critical infrastructure information
Medical, financial, and legal records held by regulated industries
If your business depends on trust, integrity, and privacy, quantum cyber threats belong on your strategic risk map.
Quantum Computing in Cybersecurity: Threats and Opportunities
Quantum computing in cybersecurity is not only a problem; it also offers new tools. Quantum technologies may help with:
Stronger random number generation
Faster detection of anomalies and patterns in large security logs
Improved secure communication over special quantum channels
But for most IT managers, CISOs, and CEOs, the urgent focus is on the downside risk: the potential for quantum computers to break the cryptography that protects the modern digital economy.
Moving From Quantum Threat to Quantum‑Safe Strategy
Once you understand what is quantum computing and why it threatens current encryption, the next step is building a quantum‑safe strategy. The good news is that security communities have been preparing for this shift for many years.
Researchers and standards bodies are developing new public‑key systems that can withstand attacks from both classical and quantum computers. These methods are often called post‑quantum cryptography or quantum‑safe encryption. They are designed so that even a large, stable quantum computer would not be able to break them in a useful time frame.
Core Principles of Quantum‑Safe Encryption
When planning your roadmap, keep these principles in mind:
Crypto‑agility – Design systems so you can swap cryptographic algorithms and keys without major redesigns.
Layered defense – Combine post‑quantum cryptography with strong symmetric encryption, access control, and monitoring.
Hybrid approaches – Use both classical and post‑quantum algorithms together during the transition period to avoid single points of failure.
Lifecycle thinking – Consider the full lifetime of your data. Ask how long it must remain confidential and whether that period overlaps with the rise of powerful quantum machines.
A thoughtful approach to post‑quantum cryptography lets you reduce risk without rushing into immature technology.
Practical Steps for IT Managers, CISOs, and CEOs
Executives do not need to become physicists to act. You only need a clear understanding of what is quantum computing doing to your business risk, and a pragmatic plan to respond. Here is a focused approach you can use with your teams.
1. Build Awareness and Ownership
Brief the board and executive team on the quantum threat and opportunity.
Assign clear ownership for quantum risk within your security or risk office.
2. Inventory Your Cryptography
Map where and how cryptography is used across systems, applications, and devices.
Identify all uses of public‑key encryption, digital signatures, and key exchange.
This inventory is often the hardest part of becoming quantum‑safe, but it is essential.
3. Classify Data by Sensitivity and Lifetime
Group data according to sensitivity: public, internal, confidential, and highly restricted.
For each group, estimate how long the data needs to remain protected.
Mark data that would still be valuable or harmful if decrypted many years from now.
The more long‑lived and sensitive the data, the higher its priority in your quantum‑safe plan.
4. Prioritize Systems and Vendors
Identify critical systems that support customer trust, revenue, or safety.
Review vendor roadmaps for quantum‑safe encryption support, especially in cloud, networking, and identity platforms.
5. Design a Quantum‑Safe Roadmap
Use the information you have gathered to design a phased program:
Phased migration approach
Stabilize your current cryptography: remove weak algorithms, enforce strong key management, and patch known issues.
Pilot post‑quantum cryptography in non‑critical systems to gain experience.
Plan upgrades for critical systems, using hybrid cryptography where appropriate.
Update policies and development guidelines to require crypto‑agility.
Throughout this process, keep asking what is quantum computing changing about our assumptions, and adjust your controls accordingly.
6. Train Teams and Communicate Clearly
Provide training for developers, architects, and security engineers on post‑quantum cryptography and quantum‑safe design.
Share clear, non‑technical explanations with business leaders and end users.
Key Takeaways for Different Leaders
Different roles will view the question of what is quantum computing through their own lens. Here are the core messages to emphasize.
For CEOs and Founders
Quantum risk is a strategic issue tied to trust, brand, and long‑term value.
You do not need to predict exact timelines; you need a credible roadmap.
For CISOs and Security Leaders
Treat quantum security risk as an extension of your existing crypto and data protection programs.
Focus first on long‑lived, high‑impact data and critical systems.
For IT Managers and Architects
Build crypto‑agility into new projects so that future algorithm changes are easier.
Avoid hard‑coding algorithms and key sizes; centralize crypto controls where possible.
Frequently Asked Questions About Quantum Computing and Security
1. What is quantum computing in simple terms?
Quantum computing is a new way of processing information that uses qubits instead of traditional bits. Qubits can be 0, 1, or a mix of both at once, which lets quantum machines solve certain types of problems much faster than classical computers. When you ask what is quantum computing in simple language, the short answer is that it is a powerful kind of computer based on the rules of quantum physics.
2. How will quantum computing affect encryption?
Quantum algorithms can, in principle, break many of the public‑key systems that protect today’s internet traffic and digital identities. This means that encrypted data captured now could be decrypted in the future once strong quantum machines exist. Understanding what is quantum computing and how it affects cryptography helps organizations decide when and how to move toward post‑quantum cryptography and quantum‑safe encryption.
3. Should organizations act now or wait?
Organizations should start planning now. You do not need to deploy new algorithms everywhere immediately, but you should inventory your cryptography, classify your data, and design a roadmap. The key is to understand what is quantum computing doing to the timeline of your current security assumptions and to avoid last‑minute, high‑risk migrations later.
4. Is all encryption broken by quantum computers?
No. Quantum computers are especially dangerous for many public‑key systems, but strong symmetric algorithms and secure hash functions can still be effective when used with sufficient key sizes. A good strategy combines post‑quantum cryptography for public‑key tasks with robust symmetric encryption and sound key management.
5. What should my next step be as a security or IT leader?
Your next step is to bring the question of what is quantum computing into your governance and planning. Align your executive team, start a cryptographic inventory, and engage with vendors and experts about post‑quantum options. By acting early, you turn a complex technical change into a manageable, phased program.
Conclusion: Turn Quantum Risk Into a Strategic Advantage
Quantum technology is moving from theory toward practical impact. The organizations that will thrive are those that ask what is quantum computing early, understand its effect on cybersecurity, and act before attackers gain the upper hand.
If you lead security, IT, or a digital business, now is the time to launch your quantum‑safe journey. Start the conversation with your team, map your cryptography, and plan your move to post‑quantum cryptography and quantum‑safe encryption. The steps you take today will help ensure that your data, your customers, and your brand remain protected in the quantum era.