Have you ever wondered how apps, cloud systems, and security platforms seamlessly talk to each other? The answer lies in APIs. But what is an API exactly, and why does it matter so much in the world of cybersecurity, IT management, and global businesses?
In this guide, we’ll break down APIs in simple terms, explore their growing role in cybersecurity and enterprise IT, and highlight key best practices leaders need to know.
What is an API?
An API (Application Programming Interface) is a set of rules and protocols that allow different software systems to communicate and share data with each other. Think of it as a messenger that delivers requests and responses between applications.
For example:
When you log into a website using Google or Facebook, an API enables the authentication.
When cybersecurity platforms exchange threat intelligence across networks, it’s done via APIs.
In short, APIs streamline digital connectivity, enhancing efficiency, security, and innovation across industries.
Why APIs Are Important for Businesses and Cybersecurity
APIs power nearly every modern digital experience. For IT managers, cybersecurity professionals, and business leaders, understanding APIs is not optional—it’s essential. Here’s why:
Integration: APIs connect organizations with third-party platforms (CRM, cloud apps, payment gateways).
Innovation: APIs enable businesses to launch new services faster, like payment apps, health-monitoring tools, or AI-driven analytics.
Security: In cybersecurity, APIs enforce access controls, monitor user activity, and detect anomalies.
Cost-Effectiveness: Instead of building everything from scratch, APIs allow companies to integrate existing solutions.
Types of APIs Every IT Leader Should Know
There are multiple forms of APIs, each serving a different function.
1. Open APIs (Public APIs)
Accessible by external developers
Enhance innovation by exposing selected functionalities
Example: Social media login integrations
2. Internal APIs (Private APIs)
Used within organizations for internal communication between systems
Increase efficiency and control over sensitive data
3. Partner APIs
Granted to specific business partners
Useful in collaborations, for example, fintech integrations
4. Composite APIs
Combine multiple services into one request
Important in complex IT ecosystems to simplify workflows
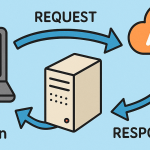
How APIs Work: A Simple Breakdown
Request – A system or application asks an API for specific data.
Processing – The API fetches or processes the data from the server.
Response – The requested data is sent back in the agreed format (often JSON or XML).
For instance, cybersecurity monitoring tools depend on APIs to fetch real-time firewall logs, malware alerts, and vulnerability reports. Without APIs, IT leaders would face huge manual data challenges.
Real-World Use Cases of APIs in Cybersecurity and IT
APIs play a critical role in cybersecurity frameworks and IT ecosystems globally.
Threat Intelligence Sharing: APIs allow cybersecurity platforms to share real-time attack data.
Identity & Access Management (IAM): APIs integrate with SSO and MFA systems to protect accounts.
SIEM Tools: Log monitoring and alerts are powered by APIs.
Cloud Security: APIs inspect, monitor, and secure cloud traffic in hybrid IT environments.
Automated Compliance: APIs help IT managers run compliance reports across industries.
Security Risks and Challenges of APIs
While APIs drive innovation, they also expand the attack surface. According to Gartner, API-related attacks will become one of the most common attack vectors for enterprises.
Common risks include:
Unauthorized Access: Weak authentication exposes sensitive systems.
Data Leakage: Poorly configured APIs may reveal confidential information.
DDoS Attacks: Malicious actors may exploit APIs to overwhelm servers.
Shadow APIs: Untracked or undocumented APIs create compliance risks.
Best Practices for Secure API Management
As an IT leader or cybersecurity professional, securing APIs should be a top priority. Here are actionable strategies:
Use Strong Authentication Methods (OAuth 2.0, API keys, JWT tokens).
Encrypt Data using TLS and HTTPS protocols.
Rate Limiting & Throttling to prevent DDoS attacks.
Regular Audits to track undocumented APIs or vulnerabilities.
Adopt API Gateways for centralized management, monitoring, and policy enforcement.
Compliance Alignment with GDPR, HIPAA, and ISO standards in sensitive industries.
The Future of APIs and Beyond
With the rise of AI, IoT, and cloud-native technologies, APIs are evolving into the backbone of digital transformation.
AI-Powered APIs: Used to provide predictive analytics and automated threat detection.
IoT APIs: Essential for secure smart device management.
Blockchain APIs: Ensuring secure decentralized transactions across industries.
Zero Trust Security: API authentication aligns with “never trust, always verify.”
APIs will continue shaping the competitive edge of enterprises while driving both efficiency and cybersecurity resilience across IT environments.
FAQs on APIs
1. What is an API in simple terms?
An API is a tool that lets two applications communicate, like how a mobile app connects with a server to fetch real-time data.
2. Why are APIs important in cybersecurity?
They allow systems to share security alerts and enforce authentication, making them vital for protecting sensitive information.
3. What are examples of APIs in everyday life?
When you book flights online, APIs fetch airline data. When you use digital wallets, APIs connect banks and merchants.
4. How do businesses secure their APIs?
By using API gateways, strong encryption, OAuth authentication, and compliance-based monitoring.
5. What is the biggest risk of APIs?
The biggest challenge is data exposure due to weak security configurations or malicious exploitation of undocumented APIs.
Final Thoughts and Call to Action
So, what is an API? It’s not just a technical term—it’s the invisible driver of modern technology and cybersecurity. APIs empower businesses to scale, connect, and innovate, while also posing new security challenges that IT managers, CEOs, and cybersecurity leaders must address.
Whether you’re developing digital products, managing cybersecurity operations, or leading global IT strategies, understanding APIs is critical for staying secure and competitive and beyond.
If your organization is exploring API strategies or needs expert guidance in API security and digital integration, now is the perfect time to act.
Get in touch with cybersecurity experts today to safeguard your digital infrastructure and accelerate innovation.